Risk management in IT vendor management is essential to minimize risks during and after the outsourcing of IT services, ensuring smooth service operations. In today’s digital world, businesses are increasingly dependent on IT services, making the efficiency and quality of these services critical to their success. In the following, we show how to effectively handle risk management for IT services during outsourcing, particularly in the operational phase as part of vendor management.
Introduction to Handling Risks in IT Outsourcing
Managing outsourcing risks is crucial for companies to maintain the stability, security, and integrity of their IT systems and data. Additionally, it helps ensuring compliance with legal and regulatory requirements. The goal of risk management in IT vendor management is to identify, assess, and mitigate risks that arise from cooperating with service providers.
Risk management should be active in all phases of the outsourcing lifecycle:
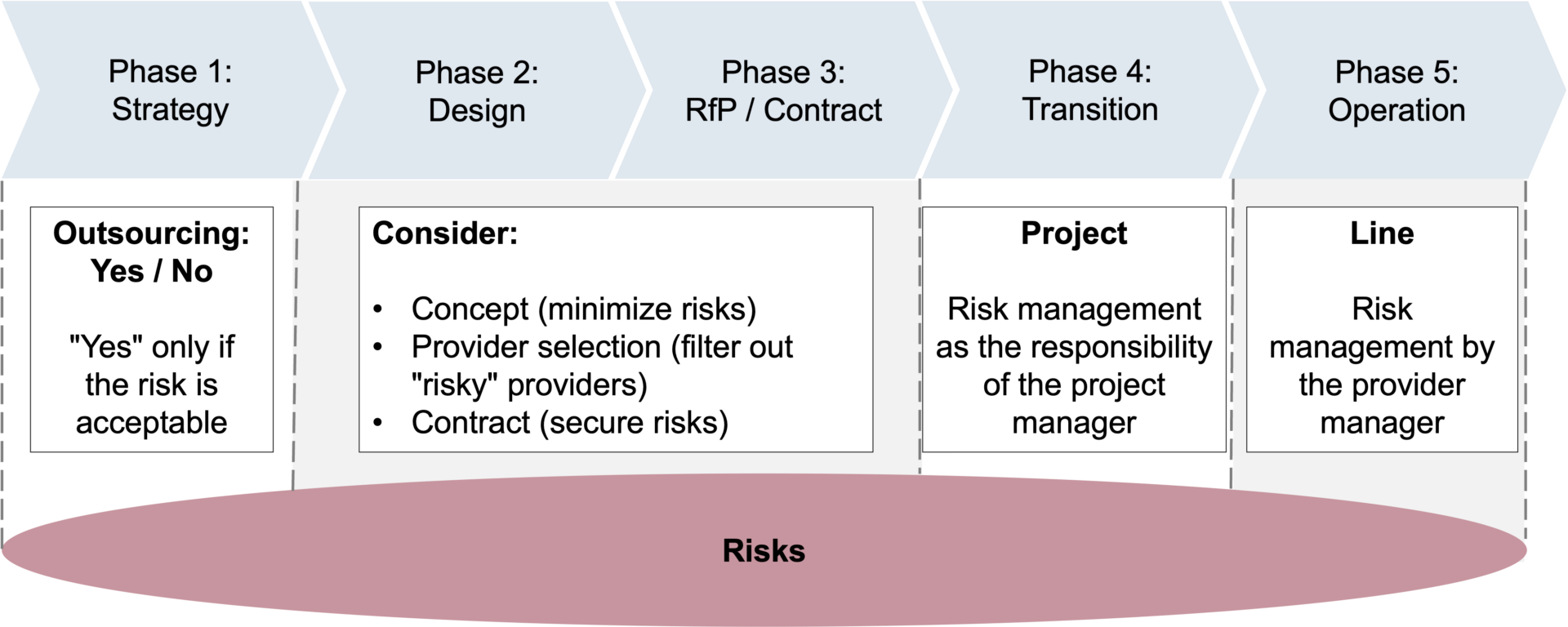
Figure 1: Outsourcing Lifecycle and Risk Management
During the “Strategy” phase, potential risks associated with the decision to outsource IT services are thoroughly examined. In the “Concept” phase, where the design of the services to be outsourced is developed, only alternatives with acceptable risks are considered.
Subsequently the “Request-for-Proposal” (RFP) phase involves evaluating provider characteristics to identify and analyze potential risks. Service provider selection is based on a balanced assessment of acceptable risks versus the anticipated benefits. Essential risk mitigation measures should be clearly defined and included in the contract with the service provider.
Finally in the “Transition” phase, risk management is integrated into project management processes. Upon completing the transition project, project managers transfer risk management responsibilities to the operational team to ensure continued oversight during the operational phase.
Legal and Regulatory Requirements
Regulated industries such as finance, insurance, and critical infrastructure (KRITIS) must adhere to strict guidelines and legal requirements for risk management in IT outsourcing. These requirements often need to be translated into specific procedures and processes within the company. Examples include:
Financial Sector
- EBA Guidelines on Outsourcing Arrangements (EBA/GL/2019/02)
- DORA (Digital Operational Resilience Act; EU 2022/2554)
- German Banking Act (Kreditwesengesetz – KWG), §25b
- Minimum Requirements for Risk Management (MaRisk) – AT 9 (a German regulation)
- Supervisory Requirements for IT in Financial Institutions (Bankaufsichtliche Anforderungen an die IT – BAIT; a German regulation)
Insurance Sector
- EIOPA Guidelines on ICT Security and Governance (EIOPA-BoS-20/600)
- German Insurance Supervision Act (Versicherungsaufsichtsgesetz – VAG), §32
- Minimum Requirements for the Business Organization of Insurance Companies (MaGo) – §13 (a German regulation)
- Supervisory Requirements for IT in Insurance Companies (Versicherungsaufsichtliche Anforderungen an die IT – VAIT; a German regulation)
Critical Infrastructure Sector (KRITIS)
- ISO/IEC 27001
- BSI Standard 200-3: Risk Management
- BMI – Protection of Critical Infrastructures – Risk and Crisis Management · Guide for Companies and Authorities
- IT Security Act 2.0
Risk Analysis for Outsourced IT Services
Risk management for outsourced IT services can be divided into two phases: before outsourcing and after outsourcing. Before outsourcing, the client is solely responsible for risk management.
After outsourcing, risks can be categorized into three groups: client risks, provider risks, and interface risks. Client risks are IT-related risks that remain with the client. Outsourcing also introduces new risks that the client must manage. Provider risks are related to the service provider and the services they offer, some of which are transferred from the client to the service provider. These risks are managed by him; however, the client remains responsible and must ensure that the service provider fulfills their obligations effectively. Organizational and technical interfaces are established between the client and provider during outsourcing, which can lead to interface risks. Clearly defining and assigning responsibilities for risk management is essential in this context.

Figure 2: Risk management before and after outsourcing
Risk Identification for Outsourced IT Services
It is also important to identify the different categories of risks associated with IT outsourcing. The risk categories help in classifying identified risks and also assist in verifying the completeness of recorded risks. The following categories may occur in particular*:
- Strategic Risk: Occurs when the decisions and actions of a service provider are not aligned with the strategic goals of the company.
- Operational Risk: Refers to the risk of loss arising from ineffective or faulty processes, employees, controls or systems of a service provider.
- Business Continuity Risk: occurs when an external event affects the service provider’s ability to continue IT operations, with corresponding impacts on the client.
- Compliance and Regulatory Risk: Results from potential non-compliance with laws and regulations by a service provider.
- Information Security Risk: Essentially concerns cyberattacks and data breaches that can occur due to security vulnerabilities at service providers.
- Financial and Credit Risk: Directly relates to a critical financial situation of the service provider, where they may fail to meet their contractual obligations, i.e., providing products and services as agreed.
- Reputational Risk: Encompasses various ways a service provider could damage the client’s reputation, brand, or name either directly or indirectly.
- Concentration Risk: Occurs when a company relies on too many high-risk or critical services from a single service provider or when there is only one provider in the market offering critical products and services to the client.
- Geopolitical Risk: Can arise when the service provider is located in a country that is prone to issues such as political unrest, corruption, or human rights violations.
- Environmental Risk: Includes political changes, natural disasters, and other social issues that can impact the service delivery of the service provider.
* https://www.venminder.com/blog/types-vendor-risks-monitor
This list is not exhaustive. Moreover the risks categorized according to risk categories should be recorded in a risk register and managed appropriately, meaning they need to be carefully assessed and suitable measures should be planned and implemented.
Sample Risk Mitigation Measures
Here are some examples of risk mitigation measures for selected risk categories:
Operational Risk:
- Clearly define responsibilities and accountabilities to minimize misunderstandings, confusion, and delays.
- Specify service levels (KPIs and target values) in the strategy and concept phase to minimize unclear expectations between the client and the service provider.
Compliance and Regulatory Risk:
- Require standards, certifications, and security systems/technologies during provider selection.
- Implement controls and processes to ensure the provider meets legal and regulatory requirements.
- Set KPIs and target values for compliance, establishing regular reporting and review.
Business Continuity Risk:
- Implementation of a Business Continuity Plan (BCP) by the service provider to ensure the continuation of IT operations in the event of an external incident.
- Regular review and updating of the BCP to ensure that it meets current needs and requirements.
- Regular testing of the BCP to ensure that it functions effectively in the event of an emergency.
Conclusion – Risk Management in IT Vendor Management
In conclusion, risk management in IT vendor management is crucial to ensure the stability, security, and integrity of IT systems and data. Moreover companies, especially in regulated industries like finance, insurance, and critical infrastructure, must adhere to strict regulatory requirements by establishing appropriate risk management procedures and processes.
Furthermore risk management should be integrated into all phases of the outsourcing lifecycle, addressing all relevant risk categories. Companies must clearly define responsibilities to manage risks that arise from working with service providers.